With the increasing adoption of DevOps practices in software development, it is essential to understand the potential security risks and vulnerabilities associated with DevOps environments.
This document provides valuable insights into attacking DevOps environments, highlighting common attack vectors, potential security weaknesses, and mitigation strategies. By understanding these attack scenarios, organizations can proactively enhance the security posture of their DevOps infrastructure.
Overview of Our Document:
This document serves as a comprehensive resource for professionals seeking to understand and mitigate security risks in DevOps environments. It explores various attack vectors, from code repositories to build pipelines and production deployments.


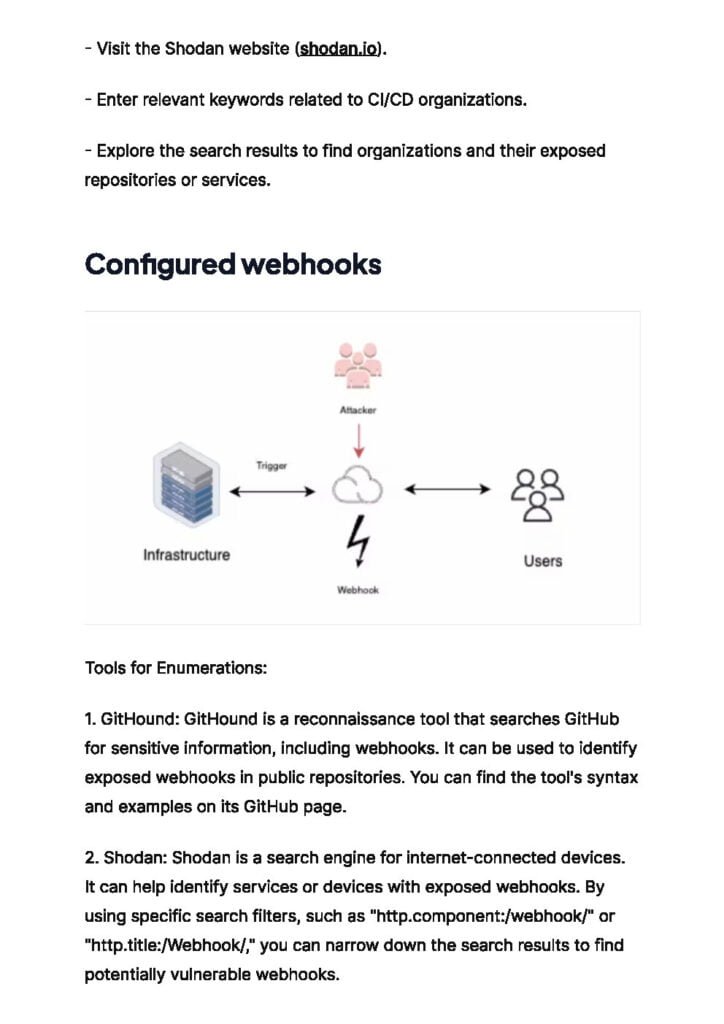

By examining these attack scenarios and their implications, this document empowers individuals and organizations to strengthen their defenses and protect their DevOps infrastructure.
The Content of the Document:
a. Introduction to DevOps Security:
This section provides an overview of DevOps security and the unique challenges it poses. It discusses the shared responsibility model, security considerations at each stage of the DevOps lifecycle, and the importance of integrating security practices into DevOps workflows. Understanding the fundamentals of DevOps security is crucial for comprehending the attack scenarios discussed in this document.
b. Attack Vectors in DevOps:
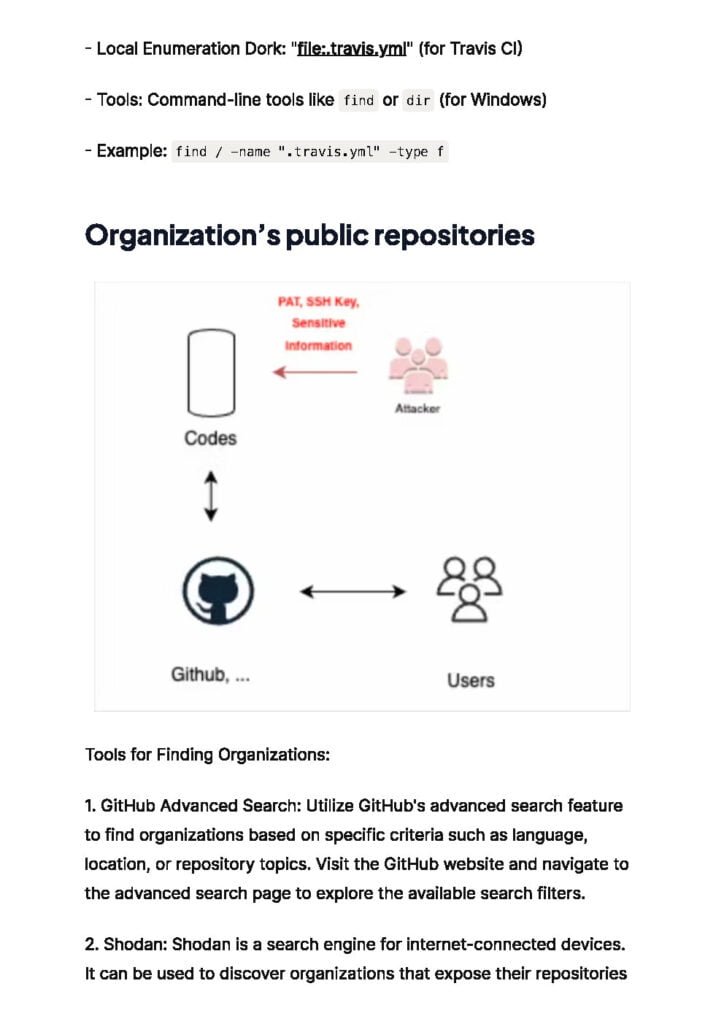
This section explores various attack vectors that malicious actors may exploit to compromise DevOps environments. It covers topics such as vulnerable code repositories, insecure build pipelines, misconfigured infrastructure, and insider threats. By understanding these attack vectors, organizations can identify potential weaknesses in their DevOps infrastructure and take appropriate mitigation measures.
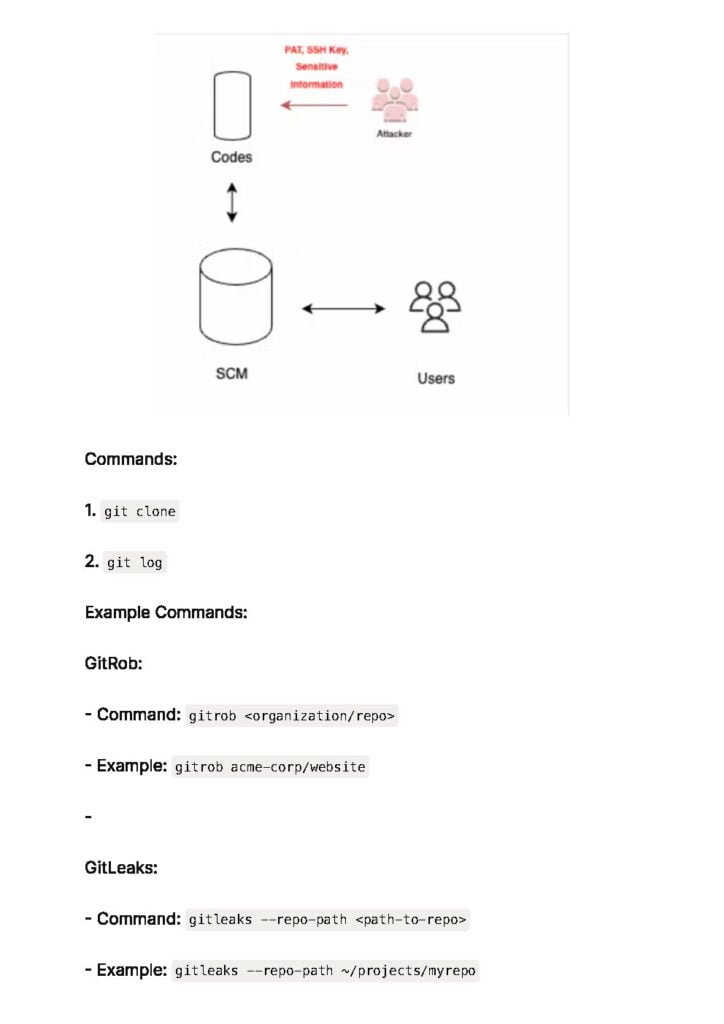
c. Code Repository Attacks:
Code repositories are a critical component of DevOps environments and can be targeted by attackers. This section examines common attacks such as code injection, unauthorized access, and supply chain attacks. It also highlights security best practices, such as implementing access controls, vulnerability scanning, and code signing, to mitigate these risks.
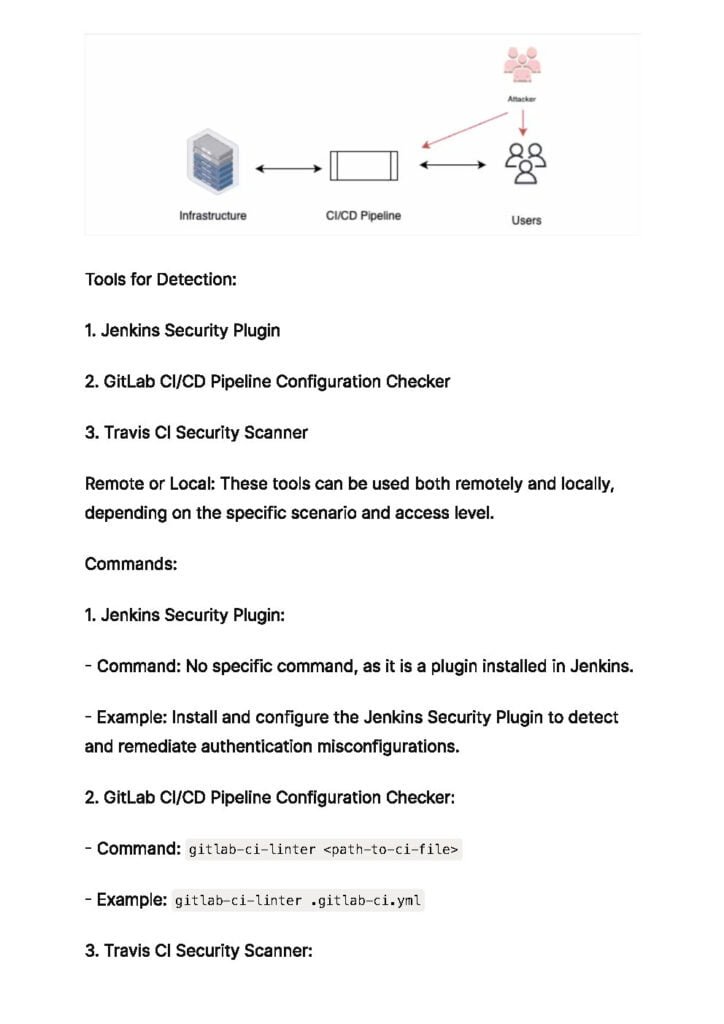
d. Build Pipeline Attacks:
The build pipeline is another potential target for attackers. This section explores attacks on build servers, insecure build configurations, and the manipulation of build artifacts. It also discusses strategies to secure the build pipeline, such as code review, secure image management, and automated vulnerability scanning.
e. Production Deployment Attacks:
Production deployments are often prime targets for attackers aiming to compromise live systems or steal sensitive data. This section examines attacks on production environments, including container escapes, privilege escalation, and unauthorized access to production systems. It also emphasizes the importance of secure deployment practices, network segmentation, and incident response planning.
Why This Document:
This document aims to raise awareness about the potential security risks associated with DevOps environments. By understanding the attack scenarios and vulnerabilities discussed in this document, organizations can take proactive measures to protect their DevOps infrastructure. It serves as a valuable resource for security professionals, DevOps engineers, and anyone involved in securing DevOps environments.
Conclusion:
Securing DevOps environments is an ongoing challenge, and understanding potential attack vectors is a crucial step towards mitigating risks. This document has provided insights into attacking DevOps environments, highlighting common vulnerabilities and suggesting mitigation strategies. By adopting a proactive security mindset and implementing appropriate security measures, organizations can protect their DevOps infrastructure and safeguard their software delivery processes.
Download From Link:
To download the full PDF document on “Attacking Against DevOps Environment,” which provides a comprehensive exploration of attack scenarios, vulnerabilities, and mitigation strategies in DevOps environments, please click on the following link: [Click Here]
Enhance the security of your DevOps infrastructure by equipping yourself with knowledge about potential attack vectors and implementing robust security practices.









